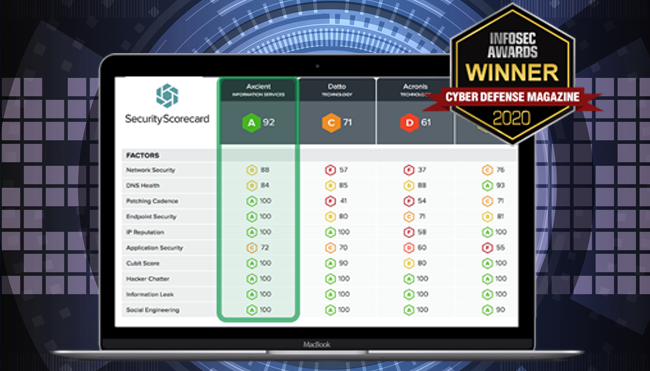
The Security Rating service is provided through our partner Security Scorecard, and aims to rate and analyze the security level of an organization, when compared to its market. Security Scorecard collects a broad range of threat intelligence data across the public Internet and dark web through its global security intelligence engine, called ThreatMarket™, which continuously collects and analyzes a broad range of highly relevant, cybersecurity signals for millions of digital assets across the internet. All the collected date is accessed through public and available proprietary security risk intelligence sources.
Security Scorecard uses both passive and active collection means to obtain the data. Active collection involves initiating a connection towards some remote host and participating in some initial part of their protocol. Passive collection can be performed in two ways; either a remote host connects to Security Score Card or the service obtains copies or summaries of some protocol transaction from a network sensor or intermediary device. The quality of data collected is directly proportional to the diversity of collection locations around the Internet combined with the frequency of data collection.
This service instantly identifies vulnerabilities, active exploits, and advanced cyber threats to ensure the business’s protection and strengthen its security posture – from an outside-in perspective, allowing to see what a hacker sees.
The analysis provided by this service focuses on:
- Network Security: examples of network security hacks include exploiting vulnerabilities such as open access points, insecure or misconfigured SSL certificates, or database vulnerabilities and security holes that can stem from the lack of proper security measures.
- DNS Health: The platform measures multiple DNS configuration settings, such as OpenResolver configurations as well as the presence of recommended configurations such as DNSSEC, SPF, DKIM, and DMARC.
- Patching Cadence: How diligently a company is patching its operating systems, services, applications, software, and hardware in a timely manner.
- Endpoint Security: relate to the protection involved in an organization’s laptops, desktops, mobile devices, and all employee devices that access that company’s network.
- IP Reputation: the platform gathers and analyze millions of malware signals from commandeered Command and Control (C2) infrastructures from all over the world. The incoming infected IP addresses are then processed and attributed to corporate enterprises through the platforms’ IP attribution algorithm. The quantity and duration of malware infections are used as the determining factor for these calculations, providing a data point for the overall assessment of an organization’s IP Reputation, along with other assessment techniques.
- Web Application Security: related to the vulnerabilities detected include Cross-site Scripting (XSS) or an SQL injection attacks.
- Cubit Score: it’s the service’s proprietary threat indicator and measures several security and configuration issues related to exposed administrative portals.
- Hacker Chatter: the platform continuously collects communications from multiple streams of underground chatter, including hard-to-access or private hacker forums, to identify the organizations and IPs that are discussed or targeted.
- Information Leak: identifies all sensitive information that is exposed as part of a data breach or leak, keylogger dumps, pastebin dumps, database dumps, and via other information repositories. The platform maps the information back to the companies who own the data or associated email accounts that are connected to the leaked information, assessing the likelihood that an organization will succumb to a security incident due to the leaked information.
- Social Engineering: identifies a variety of factors related to social engineering, such as employees using their corporate account information for services, for example, social networks, service accounts, personal finance accounts, and marketing lists that can be exploited. In addition, employee dissatisfaction is monitored through publicly available data.
The Security Scorecard service can be used by organizations of all types and sizes, and can provide different utilizations in the same platform:
- Enterprise Risk Management: through a platform that empowers organizations to discover, monitor, and report the cyberhealth of its IT infrastructure from the outside in (to see what a hacker sees).
- Third-Party Risk Management: control of third-party risk and improve the cyberhealth of the entire vendor ecosystem. Accelerate the vendor risk assessment process by 75%, with transparency into vulnerabilities in the organization’s third-party ecosystem and with industry-leading collaborative remediation tool.
- Executive-Level Reporting: Effectively communicates the organization’s cybersecurity strategy and risk to the Board and C-Suite in an easy-to-understand ratings language. Align cybersecurity with business needs, report on the organization’s performance, and demonstrate the efficacy and ROI of the cybersecurity programs.
- Cyber Insurance: Accurately assess the security posture of insureds and continuously monitor the organization’s portfolio. Leverage the largest network of rated companies to accelerate the time to quote, enhance cyber risk modeling, and provide value-added services to organization’s clients.
- Compliance: Enable cybersecurity compliance, audit remediation, and attestation with evolving regulations and industry standards. Instantly map Security Scorecard ratings to industry frameworks, track changes, and build remediation plans to remain compliant with auditors. Enables organizations to prove and maintain compliance with leading standards and regulations including PCI, NIST, SOX, GDPR, and others.
- Cyber Due Diligence: Gain insight into the cyber risk of any company, make data driven business decisions, and reduce financial risk. Perform more in-depth due diligence on an acquisition target, for a credit underwriting decision, or for a financial trade, minimizing the risk of costly cyber-related mistakes. Make prudent and risk aware financial decision.
- Service Providers: Enhance the organization’s offer with valuable Security Scorecard data. Whether the organization is a data service provider, managed service provider, or advisory service provider, the Security Scorecard Service will leverage more value to your clients.
In a nutshell, our Security Scorecard Service will provide knowledge on:
- Hackers buying and selling corporate credentials, or discussing an organization as a target;
- The health of your DNS;
- The software patching cadence efficiency of your organization;
- Employees using work email addresses on social networks;
- Common typosquat domains of an organization available on the Internet;
- How security risk changes over time;
- How an organization’s security posture ranks against competitors & peers in its industry.
It’s easy to understand this service’s main benefits, which are based on continuously monitorization of the company’s cybersecurity posture, with an analysis that enables the improvement of the decision making and limits the third–party incidents risk.